Retro Computing:
Connecting a Macintosh SE to the Internet
Introduction
So why not just use a serial connection directly from the Mac to the Rpi? I'm beginning to think I may need to try that.
Materials
- Macintosh SE FDHD
- Sacrificial Mini Din8 serial cable
- Sacrificial DB9 serial cable
- WiFi232 Modem
- Raspberry Pi Zero
- 32 GB Micro SD Card
1
Setup Raspberry Pi
/etc/ppp/options/etc/ppp/pap-secrets/etc/xinetd.d/pppd/etc/xinetd.d/telnet/usr/local/bin/ppplogin/etc/hosts.allow/etc/iptables.rules/etc/sysctl.conf
Make sure you update and upgrade your RPi operating system.
$ sudo apt-get update
$ sudo apt-get upgrade
Install telnet, xinetd, telnetd, and ppp. If you want to use ZMODEM file tranfers, include lrzsz
$ sudo apt install telnet xinetd telnetd ppp lrzsz
Allow pppd to run with elevated permissions.
$ sudo chmod a+s /usr/sbin/pppd
Create ppp user.
$ sudo useradd -m ppp
$ sudo usermod -aG dip ppp
$ sudo usermod -s /usr/sbin/pppd ppp
$ sudo touch /home/ppp/.hushlogin
Configure pppd. Backup the original files
$ sudo mv /etc/ppp/options /etc/ppp/options.orig$ sudo mv /etc/ppp/pap-secrets /etc/ppp/pap-secrets.orig
Replace options with the following in the file /etc/ppp/options
$ sudo nano /etc/ppp/options
# We will be doing PPP over Telnet - disable serial control.local# Terminate connection if remote side stops responding.lcp-echo-interval 30lcp-echo-failure 4# Debug adds a lot of detail into the system logs regarding PPP negotiation.# This is helpful in debugging client issues.debug# IP addresses to use in local:remote format. We use NAT to share# the Wi-Fi connection, make sure these are outside of your real subnet.192.192.1.1:192.192.1.2
# Other sensible optionsasyncmap 0passivenoipx
Replace pap-secrets with the following in the file /etc/ppp/pap-secrets
$ sudo nano /etc/ppp/pap-secrets
# Allow any username/password* * "" *
Configure xinetd to enable ppp over telnet in the file /etc/xinetd.d/pppd
$ sudo nano /etc/xinetd.d/pppd
service pppd{type = UNLISTEDflags = REUSEsocket_type = streamwait = nouser = rootserver = /usr/sbin/in.telnetdserver_args = -h -L /usr/local/bin/ppplogindisable = nobind = 0.0.0.0port = 2323}
Configure xinetd to enable telnet in the file /etc/xinetd.d/telnet
$ sudo nano /etc/xinetd.d/telnet
service telnet{disable = noflags = REUSEsocket_type = streamwait = nouser = rootserver = /usr/sbin/in.telnetdlog_on_failure += USERID}
And in the file /usr/local/bin/ppplogin
$ sudo nano /usr/local/bin/ppplogin
#!/bin/bash/bin/login -f ppp
Set the ppplogin script we created to be executable and enable xinetd.
$ sudo chmod +x /usr/local/bin/ppplogin
Edit /etc/hosts.allow and add the following.
$ sudo nano /etc/hosts.allow
in.telnetd:ALL:ALLOW
Enable and start xinetd.
$ sudo systemctl enable xinetd$ sudo systemctl restart xinetd
Make sure that xinetd is listening on port 2323:
$ netstat -an | grep :2323
tcp 0 0 0.0.0.0:2323 0.0.0.0:* LISTEN
Configure IP masquerading (i.e. NAT).
$ sudo iptables -t nat -A POSTROUTING -o wlan0 -j MASQUERADE$ sudo sh -c "iptables-save > /etc/iptables.rules"
File iptables.rules should look something like this.
$ cat /etc/iptables.rules# Generated by xtables-save v1.8.2 on Wed Feb 17 18:53:54 2021*nat:PREROUTING ACCEPT [0:0]:INPUT ACCEPT [0:0]:POSTROUTING ACCEPT [0:0]:OUTPUT ACCEPT [0:0]-A POSTROUTING -o wlan0 -j MASQUERADECOMMIT# Completed on Wed Feb 17 18:53:54 2021
Edit /etc/sysctl.conf and uncomment the ip_forward line
$ sudo nano /etc/sysctl.conf
# Uncomment the next line to enable packet forwarding for IPv4
net.ipv4.ip_forward=1
Create script to restore iptables rules after reboot in file /etc/network/if-pre-up.d/iptables
$ sudo nano /etc/network/if-pre-up.d/iptables
#!/bin/bashiptables-restore < /etc/iptables.rules
Make it executable and reboot
$ sudo chmod +x /etc/network/if-pre-up.d/iptables$ sudo reboot
Make sure ip forwarding is enabled.
$ cat /proc/sys/net/ipv4/ip_forward
1
Check that the masquerade rule is in place
$ sudo iptables -t nat -L POSTROUTING -nv
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)6 573 MASQUERADE all -- * wlan0 0.0.0.0/0 0.0.0.0/0pkts bytes target prot opt in out source destination
Setup Your Macintosh
Now to the Macintosh.
I'm setting this up on System 7.5.1.
MacPPP
The 68000 processor of the Mac SE prevents using Open Transport so you'll need MacPPP instead. You need MacPPP,MacTCP
You'll also need MacTCP. I'm using Glenn's MacTCP patched version 2.1 available at http://www.mactcp.org.nz/mactcp.html.
MacTCP Watcher 1.1.0
NCSA Mosaic 1.0.3
ZTerm 1.0.1
Installation & Configuration
MacTCP
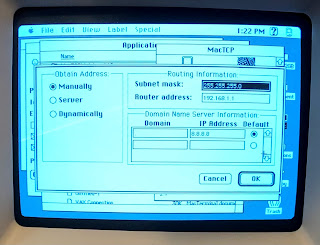
You'll need MacPPP installed before you can configure MacTCP. Obtain Address: Manually
Subnet mask: 255.255.255.0
Router address: 192.168.1.1
Domain: .
IP Address: 8.8.8.8
MacPPP
PPP Server Name: Raspberry Pi
Port Speed: 57600*
Flow Control: CTS & RTS (DTR)
Tone Dial: checked
Phone num: 192.168.1.33:2323**
Modem Init: ATNET1***
Modem connect timeout: 90 seconds
*I've tried this at 9600 to see if I was serial speed issues. 9600 is basically a safe speed to test at. Didn't make a difference in the results.
** This is the IP address of the Raspberry Pi and the port configured for the PPP interface.
***ATNET1 puts the WiFi232 modem in telnet mode.
Conclusion
I must admit, this was not entirely successful and I'm having difficulty sorting out what is wrong.
DNS works.ICMP (ping) works.
TCP does not work.
A tcpdump of the ppp0 interface when pinging google.com gives the following:
And when testing TCP, it retries several times before giving up with "TCP test to google.com failed (-23098)".
Trying with the IP address gives the same result: